In my last post, I wrote about importing MiniDV tape content to a modern computer. That leads nicely into today’s topic… because modern computers tend not to have huge amounts of local storage. We generally don’t need it, because we store our files in the cloud, and only use the local drive as a cache. But what about when you’re importing large amounts of data (say video), and you want somewhere to stage it locally, with a little more space?
I was about to throw away an old NetGear ReadyNAS Duo unit (that’s been in disgrace ever since a disk failure taught me the hard way that RAID1 is not a backup…), but then I thought it might be useful to stage some video content, before moving it somewhere safer.
Accessing the ReadyNAS
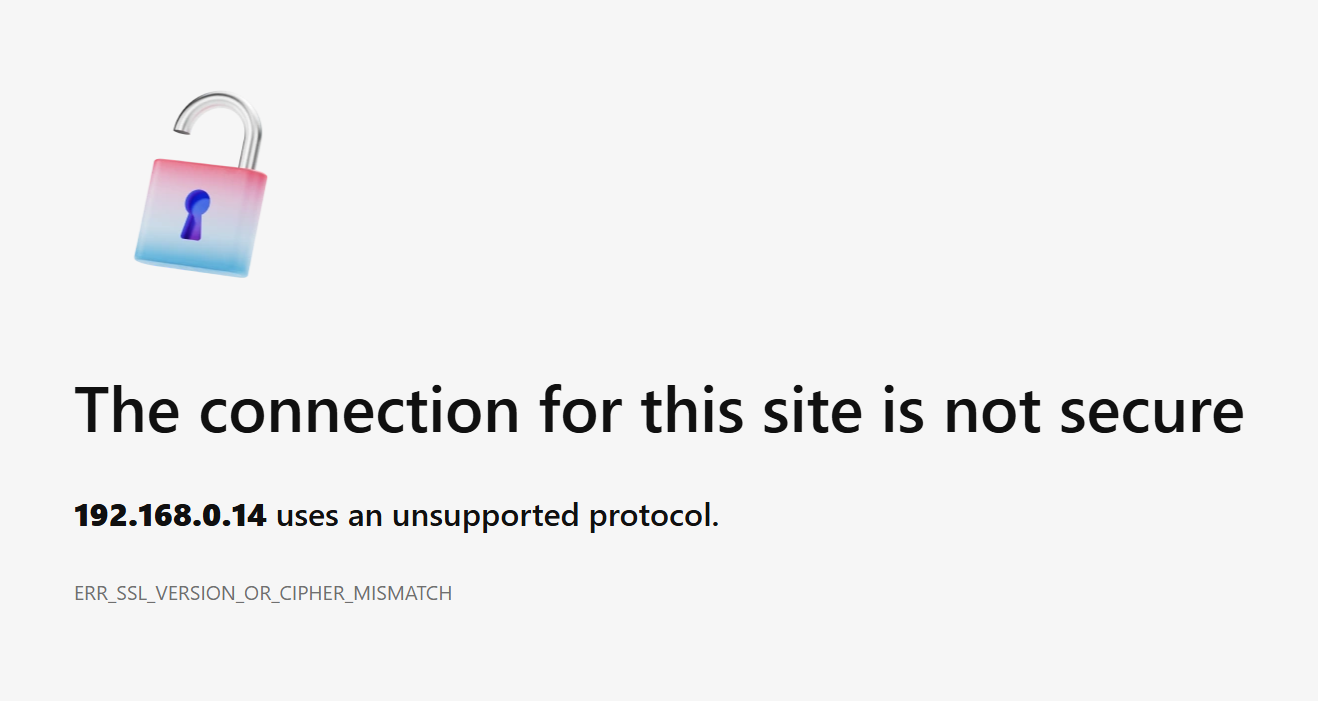
First problem was knowing what IP address it had. I managed to find that using NetGear’s RAIDar utility. But, to change the IP address (or any other settings), I needed to use the admin console. And that gave me a problem: my browser refused to connect to the site, saying that the connection was not secure and that it uses an unsupported protocol.
Well, it’s better than a modern cutesey “Something went wrong” message. It gave me a clue as to the problem – SSL version or Cipher mismatch – sounds like out of date TLS. Indeed it is, and Gøran B. Aasen wrote about the challenge in March 2022, along with a potential solution for certain ReadyNAS devices.
I’m not bothered about upgrading Apache to support TLS 1.2 – but I did still need to administer the device. I tried messing around with browser settings in Edge, Chrome and Firefox but had no luck. The transition period is over. TLS 1.0 is not supported at all. Then I had an idea… what if I installed an older browser version? And instead of installing it, what if I used a portable app version?
Tada!

So, here we go, Firefox 73.0.1 from PortableApps, via SourceForge. And I’m successfully accessing the ReadyNAS admin console.
The risk statement
For security folks who will tell me why this is a really bad idea, I know. So here’s the disclaimer. You’re only at risk when you’re using that old browser, because you didn’t install it on your system – it’s a portable app. And you’ll only use that old browser to access this one website, so when you’re not accessing the website, you’ll have closed it down, right? That way you are taking a calculated risk and mitigating it by minimising the time you have the old software running for.
As for publishing an internal IP on the web… yes, you’ve got me there…
Featured image: author’s own.
Leave a Reply